Passkeys Explained: Simple, Detailed Guide
A plain-English explanation of passkeys — what they are, how they work, why they resist phishing, and the quickest way to get started.
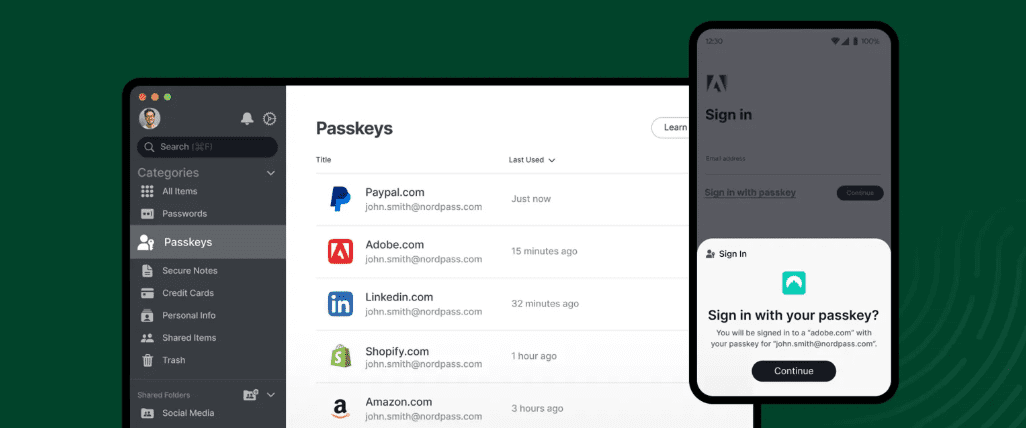
The short version: passkeys replace passwords with a key pair linked to your device and confirmed with Face ID, fingerprint, or a local PIN. There’s nothing to type or steal.
What is a passkey?
A passkey is a modern sign-in method that replaces your password. Each account has a unique public key kept by the service and a matching private key stored securely on your device. To sign in, you approve locally; your device proves you have the private key without sharing it.
Bound to the real site/app
Unique per service
Use biometrics or PIN
Public keys are harmless
How passkeys work
- Create — during sign-up or when you switch, your device generates a unique key pair for that service.
- Store securely — the public key goes to the service; the private key stays on your device (or in your chosen manager).
- Sign in — approve with Face ID, fingerprint, or a device PIN. Nothing secret is typed or sent.
Why they’re safer than passwords
Phishing: fake pages cannot request a passkey — it only works with the genuine domain.
Credential stuffing: there’s no shared secret to try elsewhere.
Database leaks: stolen public keys are useless without your private key, which never leaves your device.
Where you can use passkeys
Supported across Apple, Google, and Microsoft ecosystems, major sites (e-commerce, payments), and password managers that sync passkeys between devices.
Quick start
- Update your devices and browsers to the latest versions.
- Enable biometrics (Face ID/Touch ID, Android biometrics, or Windows Hello).
- Choose sync: platform keychain or a passkey-ready manager.
- Migrate the important accounts first (email, banking, payments, work).
- Keep recovery options for lost or replaced devices.
FAQ
Do I still need two-factor authentication?
Passkeys provide strong possession plus local verification. Some services may still offer or require extra factors — follow their guidance.
What if I lose my phone or laptop?
Use recovery options (cloud sync, hardware keys, trusted devices). Keep at least one fallback method available.
Can I use passkeys across devices?
Yes — via iCloud Keychain, Google Password Manager, or a compatible manager.
This article is general information. Always follow your organisation’s security standards and each service’s instructions.

